Implementing HSTS
(HTTPS Strict Transport Security)
Well, HTTPS (Hypertext Transfer Secure Protocol) is nowadays a must choice of internet communications protocol.
HTTPS protects the integrity and confidentiality of data between the user's computer and the site.
Users expect a secure and private online experience when using a website.
Google encourages (Secure your site with HTTPS) end-users to adopt HTTPS in order to protect one's connections to your website, regardless of the content on the site.
HTTPS protects the integrity and confidentiality of data between the user's computer and the site.
Users expect a secure and private online experience when using a website.
Google encourages (Secure your site with HTTPS) end-users to adopt HTTPS in order to protect one's connections to your website, regardless of the content on the site.
Since I started out with Cloudflare, I have to admit it that I never turned on this security feature (HSTS) HTTPS Strict Transfer Security until now.
NEW UPDATE by Cloudflare (3 days ago)
Below is the old HSTS specs which was supplanted by the abovementioned recent 2022 update.
It took me quite sometime to implement this security feature as I was not confident to do it, but with the increasing online threats, I must activate it all in full to gain the security benefits.
Last January 3, 2022, I also requested and got an online-generated report of the above-mentioned Qualys Labs SSL Test.
(For security purposes, I redacted the server information in the image screenshot above.)
(For security purposes, I redacted the server information in the image screenshot above.)
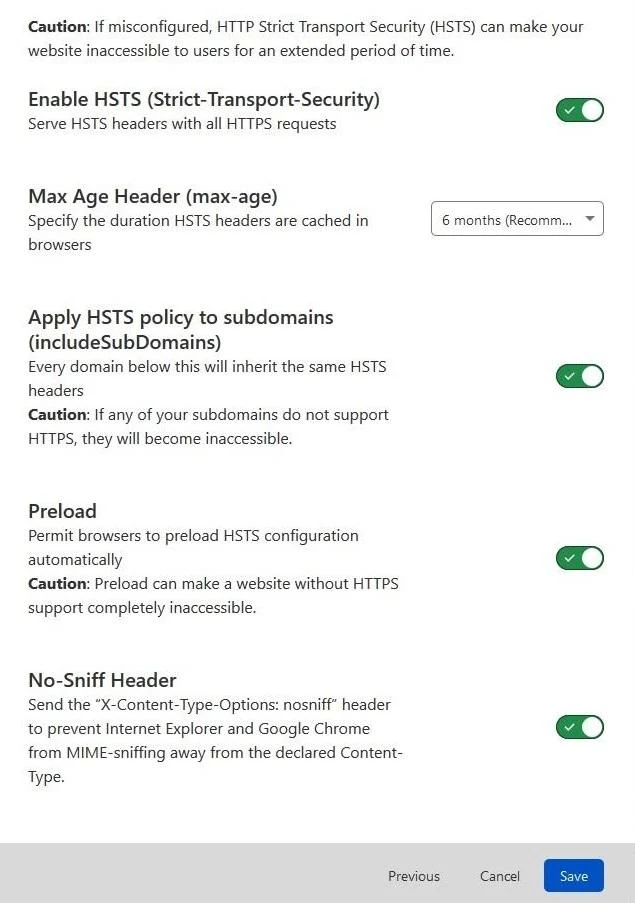
Since HSTS made mention of the parameters (configurable) which are as follows:
- Enable HSTS (Strict-Transport-Security) -Activated!
- Max Age (max-age) which is essentially "time to live" field for the HSTS header.Yes, I followed 6 months as recommended in order to earn an A+ rating from Qualys SSL Labs. (Actually, I already earned A+ a long time ago.)
- Various web browsers will cache and enforce HSTS policy for the duration of this value m. And with a value of "0," it will likewise disable HSTS.
- Apply HSTS policy to subdomains (do include SubDomains) - HSTS policies are applied to every host in a domain.
On a high note, the full implementation of HSTS (HTTPS Strict Transport Security) is a sure knockout (K.O.) punch to all threat actor's downgrade attacks.
Win a "pugilist" round by doing right, the first time.
POW! K.O. all insecure HTTP/"HTTPS" connections.
POW! K.O. all insecure HTTP/"HTTPS" connections.












Post Comment
Post a Comment